UnrealIRCD di windows
Install UnrealIRCD Di Windows
1. Login Ke Terminal Server Anda atau Remote Desktop Anda
2. Download/wget http://www.vulnscan.org/unr/Unreal3.2.8.1.exe
3. Klik 2x Unreal3.2.8.1.exe
Unread3.2.7 atau versi yang terbaru. [update]
Klik Next Untuk Melanjutkan Menginstall UnrealIRCD
Tampilan awal dari UnrealIRCD
Pilih I accept the agreement kemudian Klik Next Untuk Melanjutkan Proses Installasi UnrealIRCD
Pilih Forder Tempat Untuk Meng-Install UnrealIRCD Kemudian Klik Next
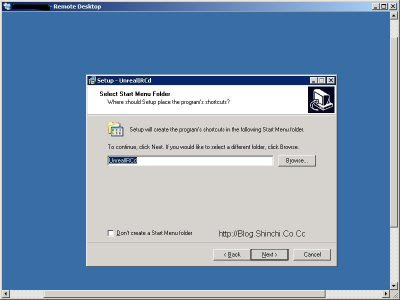
Menentukan Nama Shortcut dari UnrealIRCD kemudian pilih Next
Klik Next Untuk Melanjutkan Penginstallan UnrealIRCD
Tunggu Proses Penginstalan
Klik Finish Yang Berarti Proses Penginstalan UnrealIRCD telah selesai
UnrealIRCD telah Selesai Di Install Sekadang Tinggal KOnfigurasi Unrealircd.conf
UnrealIRCD Untuk Windows
Proses Penginstalan UnrealIRCD udah Selesai dan belum secara keseluruhan, masih ada kofigurasi dari IRCD.
4. Configurasi UnrealIRCD
Untuk Configurasi UnrealIRCD dapat di gunakan 2 macam cara :
=> Links UnrealIRCD serta oper di gabungkan dalam satu file yaitu unrealircd.conf
=> Links UnrealIRCD Serta Oper di pisah dari unrealircd.conf sehingga file config akan menjadi 3 file yaitu unrealircd.conf sebagai config utama ircd connect.conf sebagai Links/HUB dan oper.conf sebagai file Oper untuk IRCop
Contoh file unrealircd.conf
Dengan 3 File :
Contoh file unrealircd.conf
Contoh file connect.conf
Contoh file oper.conf
File Tersebut Masih Dalam format *.txt dan harus di simpah dalam file *.conf pada Folder Utama Unreal
Source: Install UnrealIRCD Di Windows
Video Tutorial Install Unrealircd Di Windows
Video List http://Video.AnakDompu.Co.Cc